Background To establish methods for reviewing and testing compliance, one must understand the structure of the law, its application, its …

Technology Research and Evaluation

Background To establish methods for reviewing and testing compliance, one must understand the structure of the law, its application, its …

Security Interoperability: A More Efficient Internet Design Research Problem:The Internet does not have a shared data architecture that allows for …
Artificial Intelligence turned 50 in 2006 (Cordeschi, 2007), making its chronological age 67 in the current year, 2023. The 1956 …
Goal of the Proposed Research Project First, the research project must be correctly referred to as a formal study or …
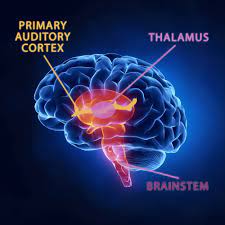
This is a short comparison of the Neurological Firing System and the Computer Intrusion Protection called the “Firewall.” It briefly …

Do you remember Napster, Gnutella, and Kazaa? These were popular peer to peer file sharing networks, where resources were pooled …
What is it? Cloud computing is computing in the clouds or using software as a service, hosted and stored somewhere …
Internet Marketing is an area of work where businesses can reach potential customers, gain exposure and grow their business. By …

What is the Internet of Things: Inter·net of things noun the interconnection via the Internet of computing devices embedded in …
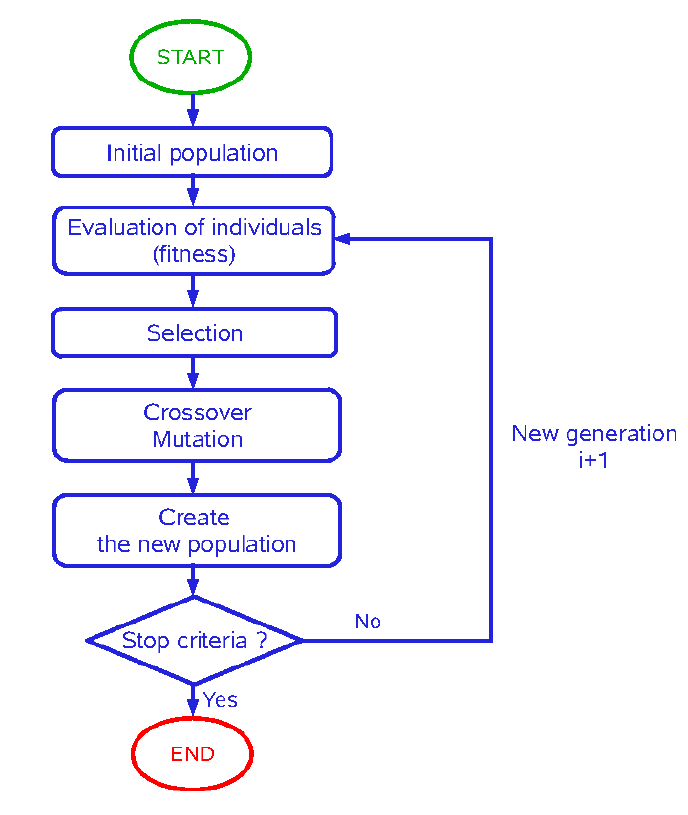
The computer currently relies on keywording and overuses it; exhausting words, targeting minds, skewing, or complicating, as an attempt to …